Author: Content Marketing team, TJC Group
Ensuring the security of systems is one of the most crucial aspects of businesses. However, with vulnerabilities hovering around, it can be challenging, especially if you have SAP systems. But worry not! In this blog, we’ve covered everything about SAP vulnerabilities and how to tackle them. Read on!
Table of contents
An overview of SAP systems
SAP systems are made up of many components that are not provided by the same company but must work together to provide the expected service. From an IT security point of view, an SAP legacy system must be kept up to date so that it does not become a weak spot in the security network of a company’s information system. Thus, according to the model proposed above, all software and hardware that make up the computer system must be updated regularly.
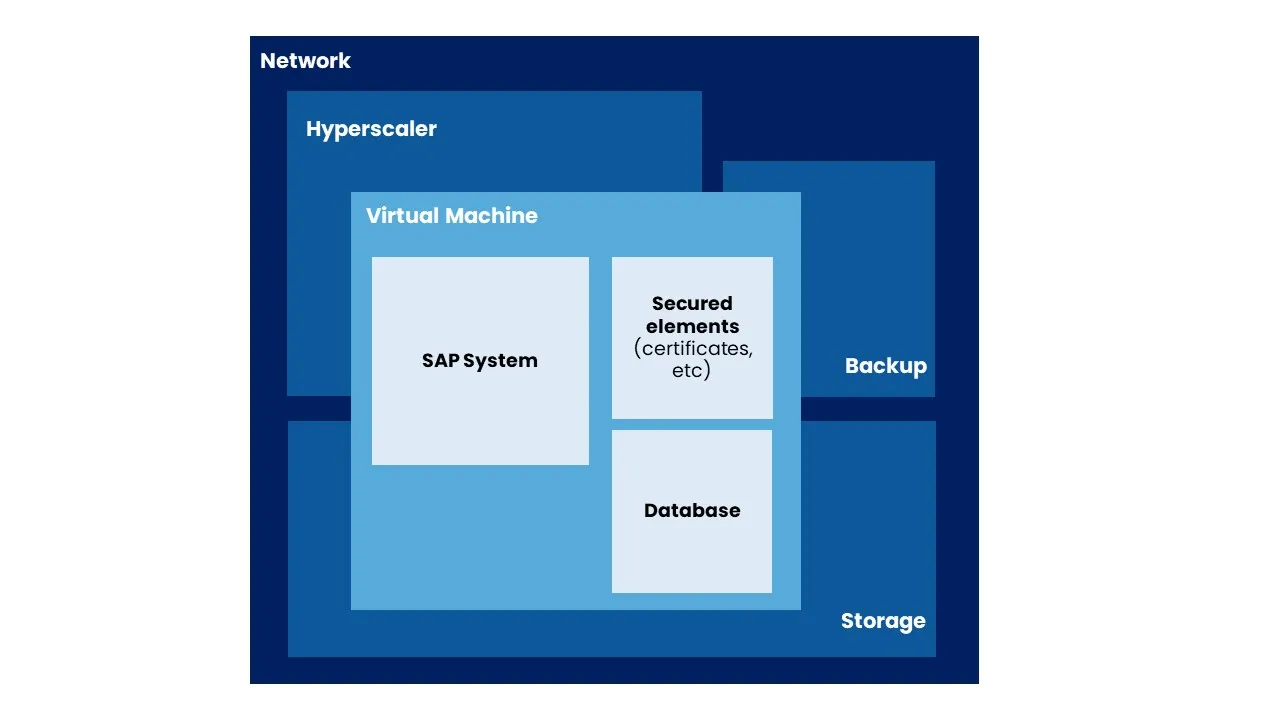
These updates can become complicated and can lead to incompatibilities or even malfunctions; since the components are not all provided by the same provider, these updates can make them incompatible with each other, preventing access to the data.
Upgrading an operating system is not always possible and may require installing a new server with a recent operating system. Hence, it is necessary to create a similar copy of the SAP system. This represents a significant workload and requires up-to-date licenses for the operating system, database, and SAP software.
System administrators are then tempted not to apply updates to the various components to avoid causing malfunctions. Critically, in such situations, the vulnerabilities are no longer correct, and therefore the system becomes vulnerable to cyberattacks.
A little in-depth about SAP vulnerabilities
For a long time, it was believed that it was enough to have robust user authorisation management in place to be protected. However, this is not the case because SAP systems regularly present vulnerabilities.
SAP publishes a vulnerability bulletin each month and reports 280 vulnerabilities per year on average over the last three years.
According to 2023 Onapsis security report, if an attacker can gain access to an unprotected SAP system by exploiting a vulnerable internet-facing application or executing an attack from inside the organisation on insecure systems, the business impact could be critical. In many scenarios, the attacker would be able to access the vulnerable SAP system with maximum privileges (Administrator/SAP_ALL), bypassing all access and authorization controls (such as segregation of duties, identity management and GRC solutions).
This means that the attacker could gain full control of the affected SAP system, its underlying business data, and processes. Having administrative access to the system would allow the attacker to manage (read/modify/delete) every record, file, and report in the system.
Key illustrative examples of SAP vulnerabilities
While these are not an exhaustive list, they correspond to serious vulnerabilities with a high level of severity and concern for the SAP system itself. The vulnerabilities can also come from the operating system, database, etc., confirming that the sources of threats can be plentiful. Keep reading to understand more about them –
The first two examples concern SAP NetWeaver:
CVE-2022-22536: SAP Note 3123396
This critical vulnerability affects the SAP system since February 2022. An unauthenticated remote attacker could exploit the vulnerability using a simple HTTP request and achieve a full system takeover. The Impacted organizations could experience theft of sensitive data, financial fraud, disruption of mission-critical business processes, ransomware, and halt of all operations.
Find further information about CVE-2022-22536 in this video: Internal Server Error: Exploiting Inter-Process Communication in SAP’s HTTP Server
CVE-2019-0328: SAP Note 2758144
This vulnerability affects the ABAP Test Cockpit (ATC) component of SAP NetWeaver ABAP. It is caused by a lack of proper validation of user input in a specific function module, which could allow an attacker to execute arbitrary code remotely. If exploited, an attacker could take control of the affected SAP system. This vulnerability was rated as critical with a CVSS score of 9.8 out of 10.
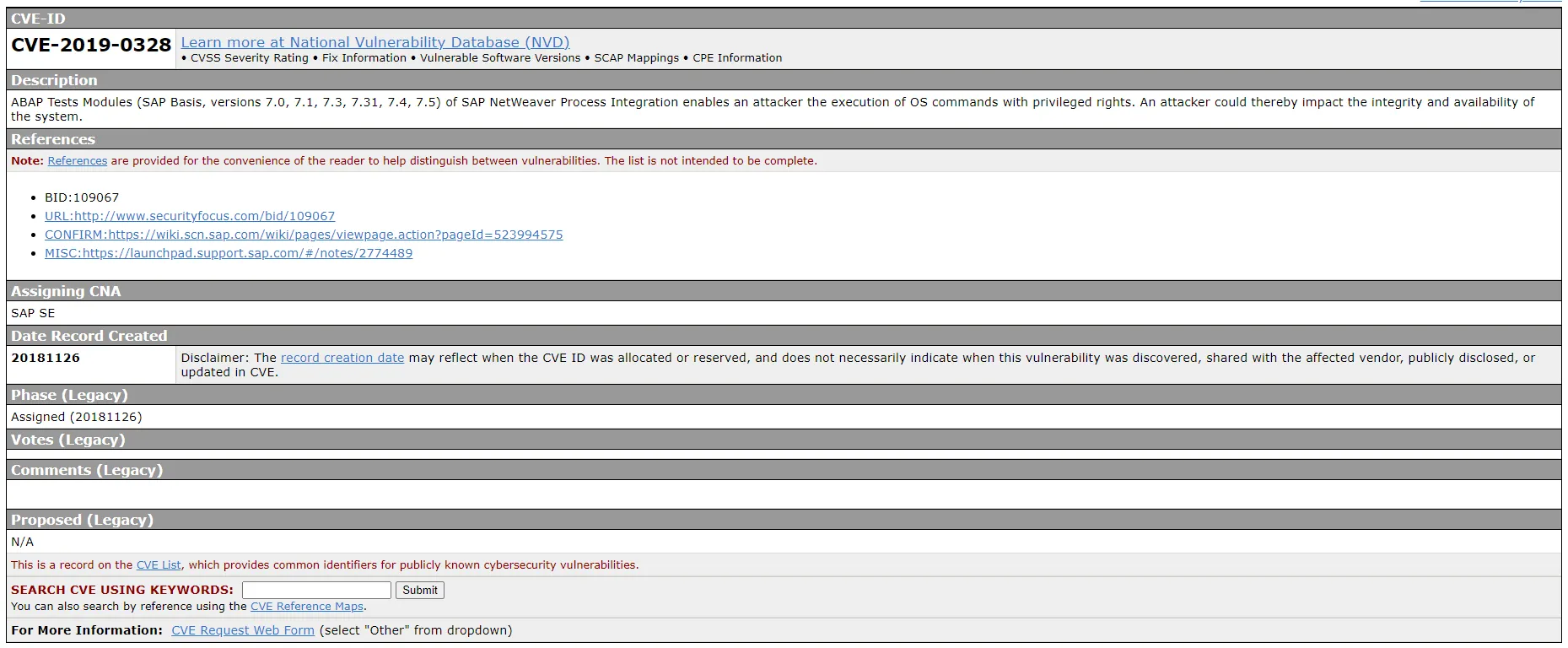
For further information about CVE-2019-0328, watch this video: SAP Code Injection Vulnerability (CVE-2019-0328)
Your SAP systems may also have NetWeaver Application Server Java, which can also be attacked through vulnerabilities:
CVE-2020-6287: SAP Note 2934135
This vulnerability was a critical remote code execution vulnerability that affected the SAP NetWeaver Application Server Java. If exploited, an attacker could seize complete control of the affected SAP system. This vulnerability was used in attacks against several organizations in the defence, aerospace, and high-tech industries. For example, a multinational technology company was targeted by attackers who exploited this vulnerability to steal confidential information related to its research and development projects.
You can find more information on CVE-2020-6287 on this video: Live Stream Hunting & Exploitation of latest CVE 2020 6286/6287 for Bug Bounties
CVE-2019-0321: SAP Note 2758146
This vulnerability allowed attackers to execute arbitrary code on SAP NetWeaver Application Server Java through a malicious JSP file. The impact of this vulnerability varied depending on the organisation that was targeted. For example, a global financial services company was targeted by attackers who exploited this vulnerability to steal sensitive information, including bank account numbers and passwords, from its systems.
CVE-2018-2380: SAP Note 2562333
This vulnerability was a critical remote code execution vulnerability that affected the XML parser in SAP NetWeaver Application Server Java. If exploited, an attacker could take complete control of the affected SAP system. This vulnerability was used in attacks against several organizations in the manufacturing, transportation, and logistics sectors. For example, a Norwegian aluminium producer Norsk Hydro was targeted by a group of hackers known as APT 29, and as a result, the company had to shut down some of its plants and switch to manual operations for a while, which caused significant financial losses.
Click on the banner below to learn how SAP legacy system decommissioning can benefit with tackling SAP vulnerabilities.
Even SAP systems for small businesses are affected by vulnerabilities and can be the target of attacks. If you are part of a large company and have the ECC version of SAP, are you sure that the Business One version is not installed and operational for an entity or subsidiary of your company?
CVE-2021-27610: SAP Note 3037518
This vulnerability allowed attackers to execute remote code on SAP Business One through a malicious file. The impact of this vulnerability varied depending on the organization that was targeted. For example, a global distributor of electronic components was targeted by attackers who exploited this vulnerability to steal sensitive information, including customer data and financial information.
SAP vulnerabilities: Important things to remember
According to Cybersecurity and Infrastructure Security Agency (CISA), in 2021 threat actors used resolved holes in unpatched SAP systems to obtain access to business networks. Therefore, the vulnerable unpatched systems must be isolated so that they do not provide an entry point for hackers. However, this is complicated to implement and maintain, making it much more difficult for legitimate users to access and interact with them.
That said, never assume that your legacy SAP system is not exposed to vulnerabilities just because it is only accessible through a VPN connection. Hackers can try to attain control or breach your systems in different ways – one of which is digital identity theft. Digital identity theft (e.g., through a targeted phishing attack) allows the attacker to bypass the VPN connection and access your SAP system as if it were exposed on the Internet.
Bear in mind that programmed obsolescence is not just a myth. As soon as the evolutions are not only software but also hardware (change of hyperscale, the evolution of the storage or backup solution, etc.), the migration can be incompatible with the legacy systems. Exceeding the MTBF (Mean Time Between Failure) of physical equipment is very risky, even if you have spare equipment. From a compliance perspective, these outdated legacy systems are black spots that will need to be monitored. Their non-compliance will be recalled tirelessly until a compliant and sustainable solution is found.
Protect legacy data with system decommissioning
All in all, it can be concluded that keeping legacy data in old systems isn’t the best idea. Because several vulnerabilities can affect an SAP system. The best way to protect your systems against such vulnerabilities is to decommission the legacy system. It stores the data in a safe environment, which means extracting 100% of your legacy data. It not only helps in securing your system but also ensures future compliance with tax, audit, and data privacy requirements.
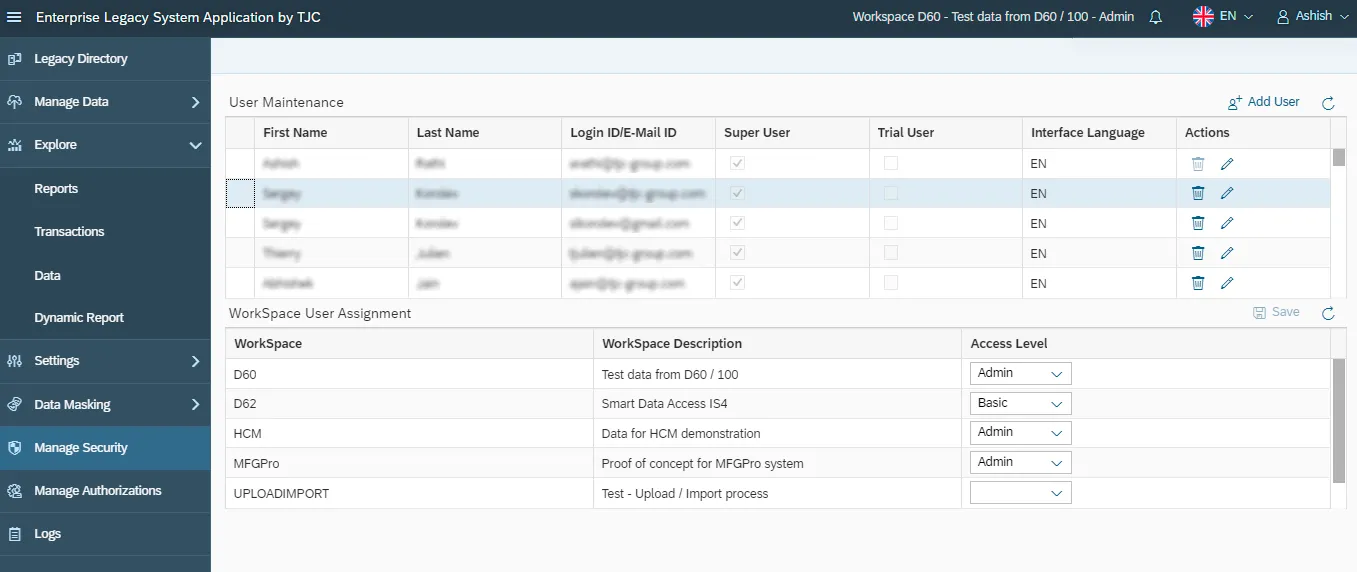
TJC Group has a proven methodology for system decommissioning. It can extract 100% of the legacy data in flat files and store it in a secured environment. Legacy data can be reassessed through an Enterprise Legacy System application (ELSA) at any point in time. Our solution gives end customers the certainty that their data is always re-accessible. The application works with both SAP and non-SAP systems.
So, if you are concerned about protecting your legacy data, get in touch with us today to know more about the same!
Learn all you need to know about Legacy system decommissioning in this webinar: https://youtu.be/SAu4qeTUNOY
Sources of information:
- 2023 Onapsis security report. https://tinyurl.com/kzrfbr5k
- Cybersecurity and Infrastructure Security Agency. https://www.cisa.gov/
- National Vulnerability Database. Results. https://nvd.nist.gov/vuln/search/results?isCpeNameSearch=false&query=SAP&results_type=overview&form_type=Basic&search_type=all&queryType=phrase&startIndex=0
Commonly asked questions
Q1. Is it safe to keep legacy data in an old SAP system?
Answer:
No, it is not safe to keep legacy data in old SAP systems as they are vulnerable to cyberattacks due to unpatched vulnerabilities. When legacy systems aren’t regularly updated, these vulnerabilities remain unaddressed, creating significant security risks for your organisation’s entire network. As a matter of fact, SAP publishes a vulnerability bulletin each month; it has reported an average of 280 vulnerabilities per year over the last three years.
Q2. What are the main security risks associated with legacy SAP systems?
Answer:
The main security risks include:
-
Critical vulnerabilities in SAP NetWeaver and other components that can allow full system takeover.
-
Attackers gaining administrative access to systems.
-
Ability for attackers to bypass all access and authorisation controls.
-
Potential for legacy data theft, financial fraud, disruption of mission-critical processes, and ransomware attacks.
-
Incompatibility issues when attempting to update components, leading to administrators avoiding critical security updates.
Q3. Why is user authorisation management not enough to protect SAP systems?
Answer:
While it was believed that robust user authorisation management was sufficient protection for SAP systems; this approach alone is inadequate because SAP systems regularly present vulnerabilities that go beyond user access controls. According to security reports, attackers who exploit these vulnerabilities can gain access with maximum privileges (Administrator/SAP_ALL), effectively bypassing all access and authorisation controls, including segregation of duties, identity management, and GRC solutions. This means attackers could gain full control of the affected system, its underlying business data, and processes.
Q4. What happens when legacy SAP systems become outdated from a compliance perspective?
Answer:
From a compliance perspective, outdated legacy systems become “black spots” that require continuous monitoring. Their non-compliance will be flagged repeatedly until a compliant and sustainable solution is implemented. Additionally, as hardware components exceed their Mean Time Between Failure (MTBF), the risk of system failure increases substantially. Even with spare equipment available, there are high potential of security risks that can result in legacy data loss or system unavailability.
Q5. What is the recommended approach for securing legacy SAP data?
Answer:
The recommended approach is to decommission the legacy system and store the data in a secure environment. This involves extracting 100% of your legacy data into flat files and storing it in a properly secured environment. TJC Group offers a proven methodology for system decommissioning that ensures your legacy data remains accessible through their Enterprise Legacy System Application (ELSA), which works with both SAP and non-SAP systems. This approach not only enhances security but also ensures future compliance with tax, audit, and data privacy requirements.









