
Table des matières
1. Introduction
Selon les rapports, le coût moyen mondial des violations de données en 2023 s’élevait à 4,45 millions de dollars, et le coût annuel mondial de la cybercriminalité est estimé à 9,5 billions de dollars en 2024. C’est dire le coût très élevé que doivent supporter les organisations du monde entier, ainsi que les atteintes à leur réputation, parce qu’un pirate informatique a décidé, quelque part, de violer des données à leur profit.
Avec l’émergence d’un nombre croissant de technologies, les cyberattaques sont malheureusement en augmentation. Il ne s’agit pas seulement de messages frauduleux ou de tentatives d’hameçonnage – le cercle est bien plus large qu’on ne le pense. Ces délits sont en augmentation dans les organisations qui traitent au maximum les technologies et les données. Mais penser que les cybercrimes ne concernent que les entreprises technologiques serait un euphémisme. Dans notre précédent blog sur les cyberattaques, nous avons parlé des différents secteurs dans lesquels les cybercrimes ont pénétré, qu’il s’agisse d’une marque de cosmétiques de luxe, d’une organisation juridique ou d’un gouvernement tout entier.
1.1 Le coût faramineux des violations des systèmes ERP
Les organisations s’appuient sur les systèmes de planification des ressources de l’entreprise (ERP) pour renforcer leurs activités, gérer le cycle de vie des produits, les processus critiques, etc. en garantissant un flux d’informations continu et ouvert.
En 2018, l’US-CERT a mis en garde les organisations du monde entier contre les cybercrimes ciblant les applications ERP, tandis que Reuters a rapporté que plusieurs systèmes dans diverses industries ont été touchés après avoir échoué dans l’installation de correctifs. Compte tenu du nombre d’acteurs de la cybermenace aujourd’hui, les attaques contre les systèmes ERP visent principalement le cyberespionnage et le sabotage – un exemple très médiatisé étant la violation du Service d’information des États-Unis (USIS).
Pour vous et moi, les systèmes ERP servent à assurer le bon déroulement des opérations commerciales. Mais pour les cybercriminels, ces systèmes sont un moyen de perturber les opérations afin de tirer des bénéfices monétaires de la faille. La raison pour laquelle les cybercriminels s’attaquent à ces systèmes est assez simple : les ERP contiennent des données sensibles et critiques pour les entreprises.
Alors, comment s’assurer que les systèmes ERP ou l’ensemble du paysage informatique sont protégés contre ces cyberattaques malveillantes et ces cybercriminels ? Une réponse efficace serait : la prévention des menaces !

2. Qu’est-ce que la prévention des menaces ?
Dans le domaine de la sécurité des réseaux et des entreprises, la prévention des menaces fait référence aux politiques et aux solutions qui protègent votre réseau d’entreprise. Par le passé, elle se concentrait principalement sur le périmètre en s’appuyant largement sur les antivirus et les pare-feu traditionnels. Cependant, face à la multiplication des menaces telles que les logiciels malveillants, les ransomwares, etc., les réseaux d’entreprise requièrent une approche intégrée et multicouche de la sécurité. Les systèmes d’exploitation obsolètes ne sont pas les seuls à permettre aux cybercriminels de cibler les systèmes. Bien souvent, les vulnérabilités des logiciels, en particulier des systèmes legacy, sont à l’origine des attaques de sécurité réseau.
Dans ce cas, les outils de détection et de prévention des menaces d’intrusion sont devenus une nécessité dans le paysage de la cybersécurité des entreprises. La suite de prévention des menaces comprend plusieurs couches d’outils cybernétiques, dont la prévention des menaces réseau, la prévention des points d’extrémité et la protection prédictive contre les logiciels malveillants sont quelques points communs.
3. Importance de la prévention des menaces
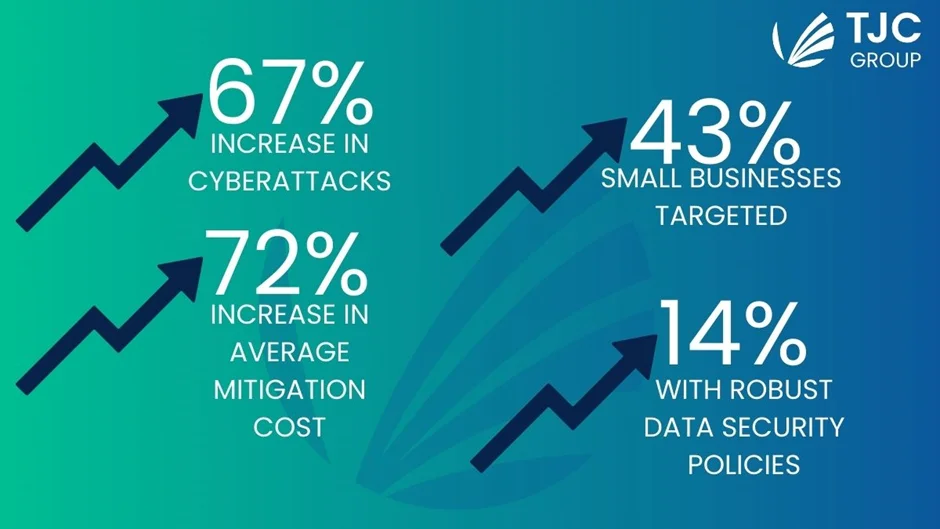
Les études montrent un nombre alarmant de fréquences de cyberattaques sur les entreprises et le coût qu’elles doivent supporter en raison de la violation. Selon une étude réalisée en 2019 par Accenture en collaboration avec l’Institut Ponemon, les violations de données ont augmenté de 67 % au cours des cinq à sept dernières années. En outre, le coût moyen des mesures d’atténuation a également augmenté de 72 % au cours de la même période. Il existe un mythe selon lequel les cybercriminels s’attaquent surtout aux grandes entreprises, car elles disposent d’informations inestimables. Pour tordre le cou à ce mythe, le rapport d’Accenture a révélé que 43 % des cyberattaques ciblent les petites entreprises, et que seules 14 % d’entre elles disposent d’un système de sécurité solide pour protéger leurs données.
L’Institut Ponemon a également publié un rapport distinct sur l’état de la cybersécurité en 2019, dans lequel il indique que 45 % des petites et moyennes entreprises considèrent que leurs politiques et solutions cybernétiques sont inefficaces en cas de cyberattaques. Plus surprenant encore, 66 % des personnes interrogées ont été la cible de cyberattaques 12 mois seulement avant l’enquête.
En 2017, Steve Morgan, de Cybersecurity Ventures, prédisait que d’ici 2021, une cyberattaque aurait lieu toutes les 11 secondes. Nous sommes en 2024, et nous connaissons la gravité et la fréquence de ces attaques – des petites entreprises aux grandes sociétés (Google, X, Meta, LinkedIn, Infosys, etc.), chaque paysage technologique a été victime de pirates informatiques. Malheureusement, il n’est pas encore possible d « être immunisé à 100 % contre les cyberattaques, mais certaines mesures permettent d » éviter la majorité des attaques sur les réseaux d’entreprise. Nous devons agir maintenant et on ne soulignera jamais assez l’importance de la prévention des menaces pour vos systèmes ERP.

4. Protégez vos systèmes ERP avec SAP Enterprise Threat Detection
Selon Forbes, il y a encore quelques années, les ERP étaient considérés comme un moyen de séparer efficacement les tâches, c’est-à-dire de prévenir les cyberaffaires dans lesquelles un employé était seul responsable d’une tâche. Cependant, le scénario a complètement changé au fil du temps, et les principaux analystes affirment aujourd’hui que la sécurité des ERP est un sujet à surveiller, car les attaques dues à des vulnérabilités critiques de ces systèmes font régulièrement la une des journaux. Je dois souligner ici que la sécurité des ERP n’est pas un sujet tout à fait nouveau, mais que le concept a considérablement évolué au fil des ans.
Pour ceux qui possèdent des systèmes ERP de SAP, la bonne nouvelle est que l’entreprise a lancé SAP Enterprise Threat Detection pour les aider à se protéger contre les attaques malveillantes. Il s’agit d’une solution de détection des menaces d’entreprise en temps réel, basée sur le cloud et personnalisée pour les applications SAP, fournie et gérée sur le réseau de l’entreprise. SAP Business Technology Platform. La solution vise à aider ses clients et partenaires à détecter les cyberattaques en temps réel en collectant, corrélant et analysant les événements anormaux et suspects dans l’ensemble du paysage SAP.
4.1 Le concept de lancement de SAP Enterprise Threat Detection
D’ici 2027, les anciens systèmes ERP seront abandonnés, laissant aux entreprises la possibilité de migrer vers le cloud ou SAP S/4HANA. La migration est une bénédiction déguisée, car elle permet aux organisations de renforcer les mesures de sécurité de leur réseau d’entreprise. Aujourd’hui, la sécurité des données et la protection de la vie privée sont de la plus haute importance, et ne pas en faire une priorité revient à mettre votre réseau en danger, ce qui pourrait avoir de lourdes conséquences à l’avenir.
Les cyberattaques contre les entreprises font partie de l’actualité quotidienne. Mais avez-vous remarqué que peu de détails techniques sont communiqués sur les couches du paysage informatique attaquées ? Comme vos systèmes ERP contiennent des données confidentielles et sensibles et qu’ils exécutent les processus les plus critiques de l’entreprise, ils deviennent une cible intéressante et de grande valeur pour les cybercriminels. Alors que les équipes de sécurité montent la garde au cœur de l’entreprise, les cybercriminels élaborent des stratégies pour pénétrer la couronne de l’organisation par le biais des couches applicatives. SAP Enterprise Threat Detection vise à détecter toute tentative malveillante sur les systèmes ERP, en alertant plus rapidement les clients et partenaires de SAP.
5. Prévenir les menaces malveillantes grâce au décommissionnement des systèmes legacy
Outre la solution de détection des menaces de l’entreprise, quelles mesures rentables peuvent être prises pour protéger vos anciens systèmes et applications ERP ? La réponse est le décommissionnement des systèmes legacy! Les systèmes non patchés sont l’un des moyens les plus faciles pour les cybercriminels d’accéder aux systèmes ERP – ils ciblent les failles et les vulnérabilités du système.
L’application de correctifs sur les systèmes nécessite une attention particulière et se complique lorsque des données héritées subsistent. Les données (systèmes) legacyprésentent un risque élevé en matière de cybersécurité car elles peuvent ne pas être cryptées ou protégées par des contrôles d’accès. On peut dire que cela rend les systèmes legacy plus vulnérables aux violations et aux cyberattaques.
Le décommissionnement des systèmes legacy peut être un processus fastidieux et compliqué. Il faut décider quelles données sont importantes et lesquelles doivent être éliminées, en particulier dans les secteurs très réglementés comme la finance ou les soins de santé, ou lors d’audits. L’une des solutions consiste à déclasser les données existantes et à les stocker à l « écart des autres bases de données critiques, de préférence dans un endroit où les cybercriminels ne pourront pas accéder. Mais là encore, la question se pose : où ? ELSA (Enterprise Legacy System Application) est une bonne option.
Conçu et développé par TJC Group, il permet de clôturer les données obsolètes tout en maintenant leur accessibilité. En termes de sécurité, ELSA est construit sur SAP BTP (la même plateforme sur laquelle est gérée SAP Enterprise Threat Detection). En outre, l’application est connectée à une base de données (telle que MySQL, PostgreSQL ou HANA Cloud) et à un stockage BLOB avec une connexion privée. L’une des meilleures caractéristiques d’ELSA est qu’il s’agit d’une application native SAP, conçue pour être utilisée avec les systèmes SAP mais également compatible avec les systèmes legacy non SAP. ELSA garantit que toutes les données patrimoniales sont stockées en toute sécurité, minimisant ainsi tout risque de cybercriminalité et bénéficiant à la fois des mesures de sécurité de SAP et de celles des principaux hyperscalers.

Sans oublier que le groupe TJC a reçu la certification ISO 27001 accordée aux entreprises qui ont mis en place un système de gestion de la sécurité de l’information solide, certifiant nos efforts pour assurer un cyber paysage solide pour nos employés et nos clients.
Contactez-nous dès aujourd’hui pour plus d’informations sur ELSA et protégez vos systèmes ERP contre les menaces malveillantes.










