Auteur : TJC Group Chief Security Officer et équipe Content Marketing
Une étude Une étude récente menée par SAPInsider auprès d’un échantillon international d’utilisateurs SAP a révélé que, bien que les attaques par ransomware soient toujours considérées comme la plus grande menace en matière de cybersécurité, une nouvelle menace les suit de près. Aujourd’hui, la menace la plus importante après les ransomwares et les attaques de logiciels malveillants est liée aux correctifs des systèmes. Ou plutôt, les menaces qui surviennent lorsque les correctifs ne sont pas mis à jour.
“Les systèmes non corrigés sont probablement le moyen le plus facile pour un cybercriminel d’accéder aux systèmes informatiques, en ciblant les failles et les vulnérabilités bien connues des systèmes”.
Points forts du rapport SAPinsider
Il s’agit là du fruit à portée de main du monde de la cybersécurité, des points d’entrée les plus évidents. De nombreuses organisations investissent des centaines de milliers de livres, d’euros et de dollars dans l’achat des dernières technologies de cybersécurité pour tenter de déjouer des attaques sophistiquées, mais ne parviennent pas à sécuriser les voies d’accès évidentes des pirates.
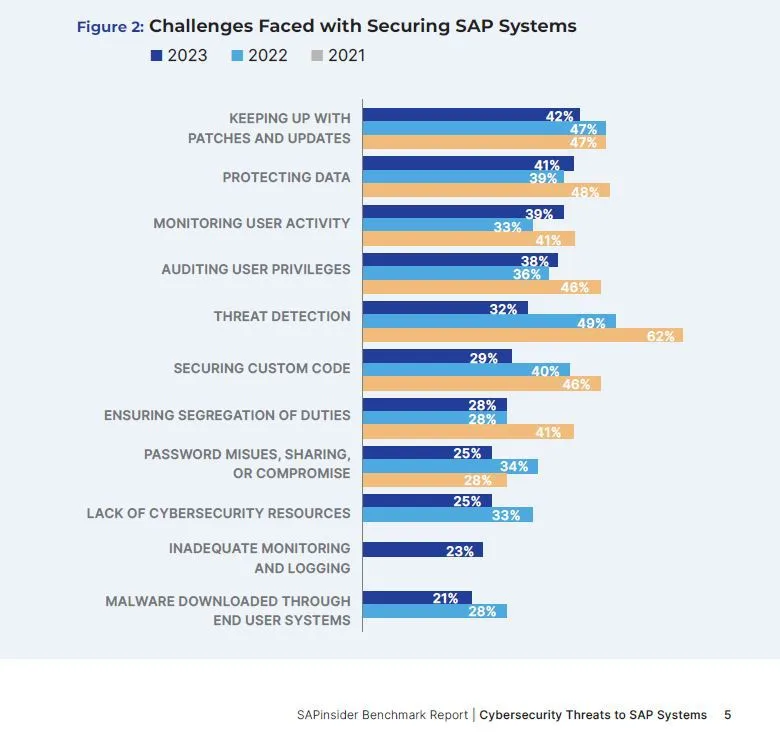
42% des organisations ayant participé à l’étude SAPinsider ont admis que le suivi des correctifs et des mises à jour était un problème permanent, qu’elles considéraient comme leur principal défi.
Pourquoi les correctifs sont-ils compliqués ?
Les problèmes qui se posent lorsqu’on essaie de planifier les correctifs sont similaires à ceux que les administrateurs rencontrent lorsqu’ils gèrent le déclassement des données existantes. Il peut être difficile de programmer un temps d’arrêt du système pour mener à bien un processus de correction (45%). Les organisations doivent gérer des priorités commerciales concurrentes (40 %) et, très souvent, les correctifs sont relégués au bas de la pile des priorités. Les services informatiques peuvent également être réticents à appliquer certains correctifs, au cas où cela aurait un impact négatif sur la disponibilité du système (40 %). Certains utilisateurs sont incapables de faire la distinction entre les correctifs les plus critiques et les moins critiques (37%) et ils peuvent disposer de ressources informatiques limitées pour appliquer les correctifs (34%) et vérifier ensuite qu’ils ont été correctement mis en œuvre.
“Très souvent, les correctifs doivent être appliqués manuellement, ce qui demande beaucoup de temps et de ressources. Le scénario peut être similaire pour le décommissionnement des systèmes legacy et, tout comme pour les correctifs, il peut être plus facile de ne rien faire, mais avec des conséquences potentiellement désastreuses pour la cybersécurité.”
Problèmes liés à l’application de correctifs aux systèmes SAP ?
La mise à jour des systèmes SAP est connue pour être un processus complexe. Il commence au niveau du matériel et des mises à jour des logiciels intégrés, progresse à travers le système d’exploitation, l’hyperviseur de la machine virtuelle (le cas échéant), la base de données et se termine par la solution SAP elle-même. Chaque mise à jour de correctif nécessite un examen individuel pour garantir son applicabilité et un plan de test pour s’assurer qu’elle résout entièrement le problème et qu’elle n’en introduit pas de nouveaux.
Spécifiquement pour les systèmes legacy SAP, il y a d’autres complications lorsqu’on envisage de patcher le système, par exemple, ne plus avoir accès au paysage DEV/QA/PRD principal, mais seulement à un système PRD en voie d’extinction. Il peut également y avoir d’autres implications en matière de gestion des vulnérabilités, car l’ancien système peut ne pas permettre l’intégration des journaux SAP dans un SIEM (outil de gestion des informations et des événements de sécurité).
Apprenez à faire la différence entre la mise hors service d’un système et le déclassement d’un système.
La question de la gestion des systèmes legacy
Lorsque l’on aborde la question des correctifs, on a tendance à penser aux systèmes actuels et productifs, car la plupart des organisations se préoccupent surtout de mettre en œuvre des correctifs pour les systèmes actuellement utilisés. Qu’en est-il des systèmes legacy ? Ceux qui subsistent mais ne sont plus utilisés régulièrement. Ceux qui contiennent des données héritées qui sont également dépassées, obsolètes et, pour certains, périmées. Ces données doivent être archivées et déclassées, mais il peut être compliqué de décider si un certain ensemble de données doit être considéré comme patrimonial, en particulier dans des secteurs très réglementés tels que les soins de santé et la finance, où il peut être nécessaire de les conserver au-delà de leur durée de vie utile.
Les données patrimoniales peuvent constituer un risque pour la cybersécurité car elles ne sont pas nécessairement cryptées ou protégées par d’autres contrôles d’accès, ce qui les rend plus vulnérables aux violations de données et au vol.
Il est beaucoup plus sûr de déclasser les données existantes et de les stocker à l’écart des autres bases de données critiques, dans un endroit où les pirates ne pourront pas accéder. Vous trouverez plus d’informations dans l’article suivant : Les vulnérabilités de SAP et les raisons pour lesquelles il n’est pas sûr de conserver des données héritées dans un ancien système SAP.
ELSA (Enterprise Legacy System Application) est une bonne option car il facilite le décommissionnement des systèmes legacy. Conçue et développée par le groupe TJC, elle entoure proprement les données obsolètes et maintient leur accessibilité. En termes de sécurité, ELSA est construit sur SAP BTP et est donc une application très sûre. En outre, l’application est connectée à une base de données (telle que MySQL, PostgreSQL ou HANA Cloud) et à un stockage blob avec une connexion privée.
Pour les utilisateurs SAP, l’une des meilleures caractéristiques d’ELSA est qu’il s’agit d’une application native SAP, conçue pour être utilisée avec les systèmes SAP, mais également compatible avec les systèmes legacy non SAP. ELSA garantit que toutes les données patrimoniales sont stockées en toute sécurité, minimisant ainsi tout risque de cyber-moldu et bénéficiant à la fois des mesures de sécurité de SAP et des principaux hyperscalers.
Dernier mot
De nombreuses organisations reconnaissent aujourd’hui qu’il est difficile de rester à la pointe des mesures de cybersécurité et consacrent une part croissante de leur budget informatique à la technologie pour tenir les cybercriminels à distance. Les clients de SAP admettent que c’est un défi, mais il n’est pas nécessaire qu’il en soit ainsi. En se concentrant sur les points faibles pour minimiser les vulnérabilités, en veillant par exemple à ce que les correctifs soient toujours à jour et en décommissionnant les données et systèmes legacy, ils peuvent contribuer grandement à la protection de leur organisation.
Le renforcement de la sécurité des systèmes legacy est l’une des principales raisons du décommissionnement des systèmes. Découvrez plus d’informations dans ce webinaire : les rouages du décommissionnement des systèmes legacy pour les systèmes SAP et non-SAP.